Security is getting more and more challenging in today’s interconnected technology environment. Cloud systems face unique risks due to their exposure to the internet and frequent integration with other systems.
Whether you use cloud security managed services, or you handle everything in-house, here’s what you need to know.
Key takeaways
- Use layered security that covers the 4 C’s (cloud, clusters, containers, and code).
- Default cloud security settings are rarely strong enough to protect cloud systems.
- Outsourced cloud security offers a better value at a lower cost compared to in-house management.
- The PoLP (principle of least privilege) is essential to controlling access to cloud systems.
What are the four C’s of cloud native security?
The four C’s of cloud native security are Cloud, Clusters, Containers, and Code. They’re nested inside each other in that order. If an attacker compromises your cloud provider, they can access your cluster, container, and code. If they compromise a cluster, they can access the container and code, and so on.
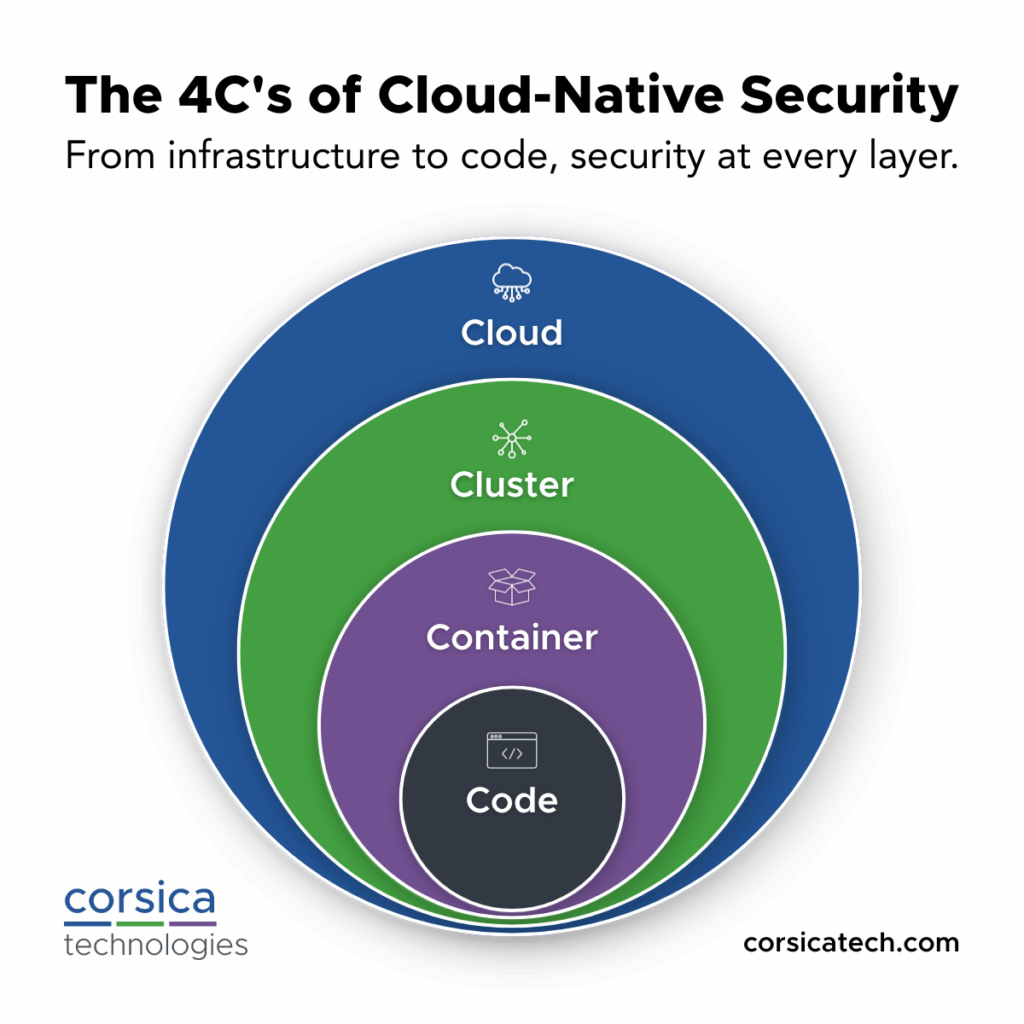
Here’s what each C means in detail.
1. Cloud
Among the 4 C’s of cloud security, “cloud” refers to the cloud environment and/or hosting provider that your organization uses.
2. Cluster
A “cluster” is a group of connected nodes (computing centers) that work together to execute a task or deliver a service.
3. Container
A “container” is a package that contains all the code, libraries, and dependencies required to run an application.
4. Code
Among the 4 C’s of cloud security, “code” is the actual computing instructions to run a process or application.
Why you need to secure all four C’s
Each layer of cloud security requires its own protection. For example, if attackers gain access to a cluster, they can potentially access every container (and thus every container’s code) that’s running in that cluster. This is why multi-layered defense is the best way to secure your cloud systems.

How is cloud security different from on-premises security?
Cloud systems present a larger attack surface than on-premises systems. Cloud security must account for more types of threats and more potential entry points. To deal with this, cloud security requires a specific set of cybersecurity controls. Some of these controls overlap with on-premises security, but others are unique to the cloud.
Here’s how the two types of security compare in detail.
| Aspect | Cloud Security | On-Premises Security |
| Infrastructure | Managed by cloud provider, but your use case may need specific configurations that are different from default configurations | Fully managed in-house or by MSP; organization and/or their MSP have complete control |
| Scalability | Highly scalable; resources can be provisioned on demand | Limited by physical hardware; scaling requires significant investment |
| Cost Model | Pay-as-you-go; operational expense (OpEx) | Large upfront capital expense (CapEx) for hardware and maintenance |
| Access Control | Remote access enabled; identity and access management (IAM) critical | Typically local access; VPNs required for remote connectivity |
| Notable Cybersecurity Controls Required (not exhaustive) | Vulnerability detection and management, vendor risk assessments, non-default cloud security configurations, web application firewall | Physical security, local firewall, Zero Trust architecture, rigorous patch management by internal IT or MSP |
| Compliance | Provider offers compliance certifications; customer must configure them properly or engage an MSP to do so | Full responsibility for meeting compliance standards (or engaging an MSP to do so) |
| Threat Surface | Broader attack surface due to internet exposure | Smaller attack surface; mostly internal network |
| Incident Response and Containment | Can be partially automated | Requires full manual response |
| Disaster Recovery | Built-in redundancy and geographic distribution, though your use cases may require specialized disaster recovery plans and resources | Requires dedicated DR site, manual failover, and dedicated plans, roles, and resources either managed internally or by an MSP |
How do managed cloud security services compare to in-house security?
Managed cloud security services generally provide more value at a lower cost when compared to in-house management of cloud security. An MSP (managed service provider) offers access to an entire team of cloud security experts, usually bundling this service with others like managed IT services, cybersecurity, EDI, and data integration. These bundled services typically cost about the same as one staff hire. This creates significant cost savings, as cloud security experts command high salaries.
Here’s how the two approaches compare in detail.
| Aspect | In-House Cloud Security Management | Outsourced Cloud Security Management |
| Control | Full control over policies, tools, and processes | Some control via SLAs/policies; execution governed by provider’s standards |
| Expertise | Requires hiring/retaining skilled cloud security professionals | Access to specialized experts and current threat intel without internal hiring |
| Cost Structure | Higher fixed costs (staff, tools, training); variable with growth | Predictable subscription/service fees; economies of scale |
| Scalability | Scaling needs budget approvals and internal headcount | Scales quickly using provider’s capacity and staffing |
| Response Time | Varies with team coverage and workload | 24/7 monitoring and incident response (typically SOC-backed) |
| Compliance | Full responsibility for implementing and maintaining compliance (e.g., ISO, PCI-DSS, SOX, SOC 2, HIPAA, etc.) | Provider offers mapped controls, evidence support, and audit-ready reporting for all major compliance frameworks |
| Patch Management | Team must evaluate, test, and deploy patches and new detections | Provider manages patches, updates, tuning, and emerging detections across clients |
| Risk Management | Customized risk appetite and control design; maturity depends on internal rigor | Standardized risk methodologies, playbooks, and SLAs; scope limited to contract terms |
| Vendor Lock-in | Less tied to a service provider; still locked into chosen tools/clouds | Potential dependency on provider’s platform, data schemas, and processes; negotiate exit/data portability upfront |
| Customization | Deep customization of detections, workflows, and integrations | Usually packaged services; customization via SOW/change requests, which may increase cost or timeline |
What are the best practices for cloud security?
Cloud security requires a comprehensive approach to risk discovery and management. This gets complicated in a world of interconnected cloud systems and vendors, which is why many organizations turn to managed cloud security services.
Here’s a checklist of cloud security best practices.
- Don’t assume default cloud security controls are sufficient; scope out your needs and implement any unique configurations required.
- Conduct regular penetration testing to uncover vulnerabilities in complex cloud architectures.
- Establish vulnerability management processes to prioritize and remediate vulnerabilities.
- Establish regular cybersecurity training for every employee in your organization.
- Establish an incident response plan so you know who does what if a cyberattack occurs.
- Implement disaster recovery and business continuity plans to recover your data and continue operating after a cyberattack.
- Establish and maintain regulatory compliance to reduce your attack surface and your potential legal liability.
- Analyze integrated cloud vendors for risk and remediate any vulnerabilities found.
- Implement MDR (managed detection and response) to catch potential threats and lock them down before they activate.

How can roles and access controls be used to protect data in cloud applications?
The principle of least privilege (PoLP) is an excellent guide for protecting data in cloud applications. The principle states that a user, system, or application should never have more access or permissions than it requires to execute its responsibilities.
Here are a few examples.
- An intern working in the marketing department doesn’t need access to company financial systems.
- A warehouse manager doesn’t need access to the backend of the company website.
- A cloud application for logging sales calls doesn’t need access to operational technology on the shop floor.
Rigorously implementing PoLP is a great way to protect data that lives in cloud applications.
How do I know what data is being shared outside the cloud environment?
Use an application that tracks the sharing of data outside a specific cloud environment. For example, if your organization uses Microsoft products, Microsoft Defender for Cloud Apps helps you understand where data is potentially being exposed outside your environment.
Of course, you need more than a software solution to manage this risk. You also need a team of cloud experts who can monitor the software, understand what it says, and take action as needed. This is one of the primary reasons that companies choose a managed cloud security provider like Corsica Technologies.
Will the cloud provider’s native security tools be enough to protect my data and services, or should I use additional third-party protection?
Default security settings in cloud systems are rarely adequate to address an organization’s unique risks while minimizing operational friction. While common strategic principles apply across all cloud environments and use cases, a good strategy is specific, adapted to the strengths and weaknesses of a real organization.
Implementing and maintaining this kind of cloud security strategy requires bandwidth and expertise. This is one of the main reasons that organizations turn to managed security services provider (MSSP) like Corsica Technologies to take ownership of cloud security.
How do I secure my cloud accounts against insider threats and ransomware?
While an insider threat can lead to a ransomware attack, these are two different types of attacks, and each one requires specific cybersecurity controls to prevent it. Here are the most important controls for each type of attack.
Cloud security controls to stop insider threats
- Identity and permissions management
- Access controls
- User behavior monitoring
- Cybersecurity awareness training
Cloud security controls to stop ransomware
- Email security controls
- Phishing awareness training
- Vulnerability detection and management
- Patch management
- MDR (managed detection and response)
The takeaway: Go beyond default security
Default security settings are rarely enough to protect cloud systems. The modern technology environment is complex, interconnected, and vulnerable to attack. Cloud security requires a comprehensive strategy, the right controls, and expert resources to keep you secure. That’s why companies turn to Corsica Technologies. We’ve helped 1,000+ clients solve their problems with technology. Get in touch today, and let’s secure your cloud systems.

Ready to secure your cloud systems?
Reach out to schedule a consultation with our cloud security specialists.













