Originally published Nov 3, 2020. Last updated January 14, 2026.
HIPAA forever changed the handling of PHI (protected health information) when it became law in 1996. However, the regulation was drafted long before anyone could envision the future complexity of cybersecurity in the healthcare industry.
The HITECH Act solves this problem. It builds on HIPAA, pushing the healthcare industry to adopt electronic records.
In 2026, HHS is set to modify the HIPAA Security Rule significantly. While these requirements aren’t finalized as of this writing, it’s important for covered entities to understand them and start preparing.
Here’s how HIPAA relates to HITECH in detail in 2026.
Key takeaways:
- HITECH makes HIPAA more effective at protecting PHI.
- HIPAA violation penalties follow a tiered structure based on severity. The 2024 adjustments to the fine structure are still in effect in 2026.
- HHS will overhaul the HIPAA Security Rule in 2026, with required compliance dates not yet determined.
- Covered entities should start understanding these changes now so they have time to prepare.
- Covered entities need a comprehensive approach to establishing and maintaining HIPAA cybersecurity compliance–one that covers encryption, systems, policies, training, and more.
Why is the HITECH Act important to HIPAA compliance?

In 2009, President Obama signed the HITECH Act into law. As it relates to HIPAA and cybersecurity, this Act introduced direct accountability for business associates of covered entities who disclose protected health information in a way that doesn’t comply with HIPAA. In other words, it made HIPAA more effective at actually protecting PHI.
HITECH also gives patients the right to request the release of their ePHI (electronic PHI) if that information is available electronically. In addition, HITECH introduced rules regarding the disclosure of any security breaches affecting PHI. HITECH also incentivized organizations to adopt EHR (electronic health records). Last of all, HITECH introduced more stringent and graduated fines for organizations that fail to secure PHI.
Prior to the HITECH Act, only 9% of hospitals and healthcare facilities had adopted EHRs. To boost efficiency and patient care coordination between different entities, the Act incentivized organizations to transition to electronic health records.
Such projects aren’t cheap. The initial cost of implementing the new technology proved to be too much for many healthcare providers. To overcome this roadblock, the HITECH Act introduced incentives to encourage healthcare providers to make the change. The Act increased the rate of adoption to EHRs from 3.2% to 86% in nine years.
To be clear, HITECH didn’t make HIPAA compliance mandatory—that was already the case after the establishment of HIPAA in 1996. However, HITECH made sure that non-compliant entities could receive a substantial fine. The Act also pushed organizations to comply with HIPAA privacy and security rules by implementing safeguards to keep health information such as PHI private and confidential, restricting uses and disclosures of health information.
The main differences between HITECH and HIPAA are the penalty structures and the responsibility of breach notifications.
Breach notifications
To implement certain provisions of HITECH, Health and Human Services (HHS) introduced the breach notification rule. This regulation requires health care providers, health plans, and other entities covered by HIPAA to notify individuals when their health information is breached. If a breach affected less than 500 records, there is no time limit for reporting it. For any breach affecting more than 500 records, the organization has 60 days from the time of discovery to notify HHS, the media, and the State Privacy Officer.
The organization must also send a first-class mailing to all breached patients addressing what happened to them personally and what the organization is doing to resolve the breach. In some cases, the organization may pay for breached patients to get free access to their credit reports.
Essentially, HITECH extends legal liability for a breach to any entity that handles PHI or ePHI.
Original HITECH penalty structures for HIPAA violations

The HITECH Act changed the penalty structure for covered entities found to be noncompliant with HIPAA. Previously, the fine structures allowed noncompliant companies to pay the fines and continue on their merry way. HITECH introduced much harsher fines with violation tiers, making it much harder to just pay the fine without addressing the issue.
When the law was passed, it introduced a set of tiered fines ranging from $100 to $50,000 per violation while setting the maximum fine at $1.5 million. However, the fine schedule was updated in 2023 for all violations occurring on or after November 2, 2015.
What are the penalties for HIPAA noncompliance in 2026?
The current fine structure was last updated August 2024, and it’s still in place for 2026. It’s structured around four tiers reflecting the level of neglect that led to the violation:
- Tier 1: Organization was unaware, and the breach could not have been discovered through due diligence.
- Tier 2: Reasonable cause that the organization should have discovered the violation by exercising due diligence.
- Tier 3: Willful neglect of HIPAA regulation, but the organization corrected the noncompliance within 30 days of discovery.
- Tier 4: Willful neglect of HIPAA regulation, and the organization did not correct noncompliance within 30 days of discovery.
For each tier, there is range of applicable fines per violation as well as an annual cap per violation type. Here’s how those fines play out at different tiers.
HIPAA noncompliance fine structure for 2026
| Tier | Description | Penalty per Violation | Annual Cap (per violation type) |
| Tier 1 | Lack of Knowledge | $141 – $35,581 | $35,581 |
| Tier 2 | Reasonable Cause | $1,424 – $71,162 | $142,355 |
| Tier 3 | Willful Neglect (But corrected within 30 days of discovery) | $14,232 – $71,162 | $355,808 |
| Tier 4 | Willful Neglect (Not corrected within 30 days of discovery) | $71,162 – $2,134,831 | $2,134,831 |
Note how Tier 1 and 2 emphasize the exercise of due diligence. If the organization decides not to conduct due diligence, and they’re aware of the violations, they could land in Tier 3 or 4 because of willful neglect.
How do we improve compliance with HIPAA and HITECH in 2026?

HHS is updating the HIPAA Security Rule in 2026, with plans to finalize the rule in May. While the new stipulations aren’t finalized and don’t have a compliance deadline in place yet, organizations should begin examining them now, building a compliance plan in 2026.
Note: If you need help determining where you stand, Corsica Technologies can assist with a compliance gap assessment. Just reach out to us to get started.
Here are the high-level actions that organizations can take to prepare for compliance with the modified Security Rule.
- Prepare for the removal of “required” vs “addressable” distinctions. Nearly all implementation specifications are expected to become mandatory, with narrow exceptions.
- Prepare to create and maintain comprehensive written documentation. Organizations will need all-encompassing documentation on policies, procedures, plans, analyses, and compliance activities relating to the modified Security Rule.
- Prepare for required asset inventories and network mapping. Organizations will need to maintain comprehensive IT asset inventories as well as network maps that illustrate how ePHI moves through their systems.
- Prepare for a formal compliance audit every 12 months. This requirement will force covered entities to make HIPAA security compliance part of every operational process, day in and day out.
- Prepare for more stringent cybersecurity requirements. Mandatory MFA for all users, role-based access, session timeout, and many more security controls will become required. (See below for details.)
- Prepare for enhanced requirements to BAAs (business associate agreements). BAAs will have to specify how they comply with all the new cybersecurity requirements. Blanket statements will no longer be acceptable.
- Prepare for expanded and more detailed risk assessments. These will be required every 12 months—with more detail and documentation than ever before. Covered entities can get a leg up on this requirement by aligning with the NIST Cybersecurity Framework.
How do we comply with the modified Security Rule in 2026?
So far in 2026, requirements for Security Rule compliance haven’t actually changed. However, HHS is set to modify the Security Rule significantly in 2026, with compliance dates expected to follow. Covered entities should start examining the new requirements now and planning how they’ll achieve compliance.
Here are the new cybersecurity requirements that HHS is expected to add to the Security Rule in 2026. NOTE: Corsica Technologies can help you achieve all of these.
- MFA (multifactor authentication) required for all system access, whether remote or onsite.
- Role-based access controls would be required.
- Automatic session timeouts would be required.
- Revocation of system access within one hour of workforce termination would be required.
- Encryption of ePHI in transit and at rest would be required rather than “addressable.”
- A 24-hour incident reporting timeline would now be required.
- A written incident response plan, along with annual incident response testing, would now be required.
- Covered entities would be required to demonstrate the capability to restore critical systems within 72 hours of an incident.
- NIST-aligned security practices would now be required.
- Vulnerability scans would be required every six months.
- Penetration testing would be required once a year.
FAQs about HIPAA and HITECH
What is protected health information (PHI)?
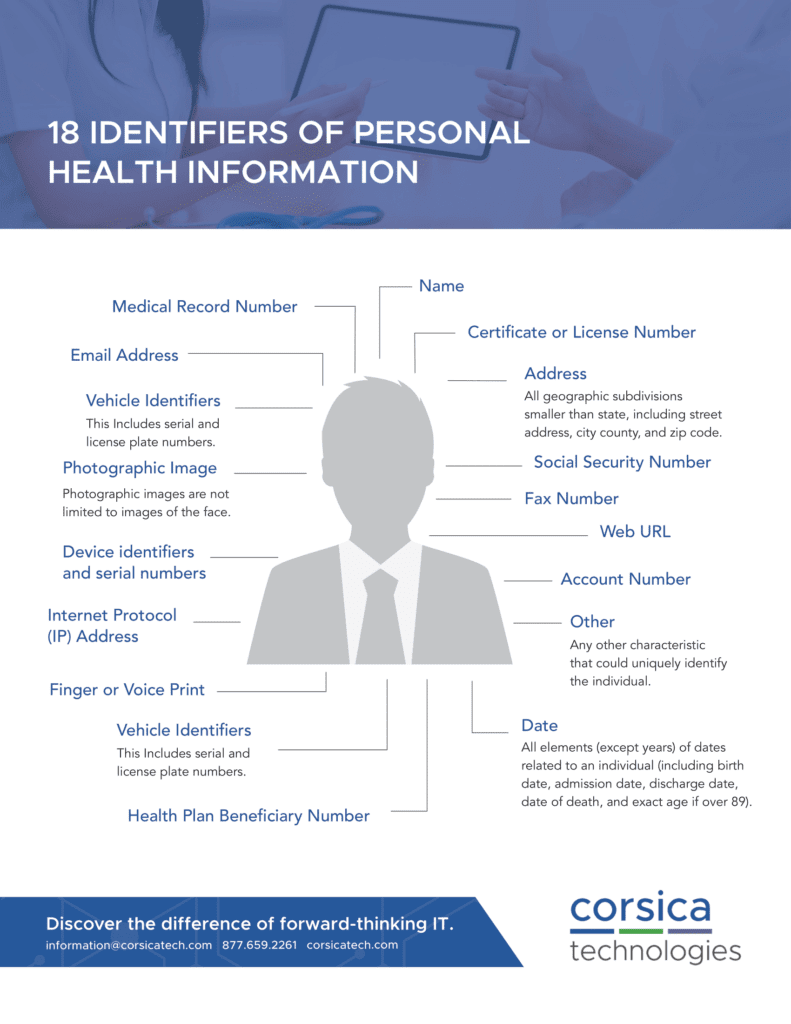
Information collected from an individual by a covered entity that relates to the past, present, or future health or condition of an individual and that either identifies the individual or there is basis to believe that the information can be used to identify, locate, or contact the individual.
What is HITECH and when did it go into effect?
HITECH stands for the Health Information Technology for Economic and Clinical Health (HITECH) Act. President Obama signed it into law on February 17, 2009.
The HITECH Act provided over $30 billion for healthcare infrastructure and the adoption of electronic health records (EHR). According to the Act, physicians were eligible to receive up to $44,000 per physician from Medicare for meaningful use of a certified EHR system starting in 2019. This support expired in 2021.
What businesses must comply with HIPAA laws?
Any business entity that electronically processes, stores, transmits, or receives medical records, claims or remittances must comply with HIPAA. This can include organizations such as staffing companies, HR departments, and other entities outside of a standard healthcare facility.
How long must HIPAA Compliance Records be retained?
HIPAA requirements preempt state laws if they require shorter periods of document retention. HIPAA compliance states you must retain required documentation for six years from the date of its creation or the date when it last was in effect.

Want to learn more about HIPAA, HITECH, and data security?
Reach out to schedule a consultation with our HIPAA security specialists.












