
9 Common Signs of a Phishing Attack
Phishing is a social engineering tactic cybercriminals use to lure sensitive data via emails. Take our Quiz & see if you recognize phishing red flags.
You get a single team handling cybersecurity, IT, and data integration services like EDI, filling the gaps in your team.
“Corsica is a one-stop shop for us. If I have a problem, I can go to my vCIO or a number of people, and you take care of it. That’s an investment in mutual success.”
– Greg Sopcak | Southern Michigan Bank & Trust
From 24/7 SOC services to MDR/SIEM, penetration testing and training, we’ve got you covered.
Get the expert support you need for your network, on-premises devices, VoiP, M365, Google Workplace, and everything in between.
Full support of compliance frameworks, including CJIS, HIPAA, CMMC, NIST, SOC 2, and more
Cut through the hype with smart strategies and right-fit AI solutions for your organization.
Take strategic steps with confidence as you collaborate with our expert business and vCIO consultants.
Get cloud security, integration, server virtualization, and optimization strategies to reduce your cloud costs.
Connect any data source to any other with robust solutions and managed services.
Stay ahead of the curve, eliminate waste, and grow revenue with next-generation technologies.
Expert consulting, implementation, integration, managed services, and cybersecurity for Microsoft products.
One program. One partner. Complete AI transformation.
It takes dedicated experience to use technology strategically in your industry. That’s why we specialize in certain verticals while offering comprehensive technology services.
From webinars and video tutorials to guides and blogs, we’ve got resources to help you and your team address any technology challenge.
Employees are your front line of defense in today’s cyber threat landscape. Give them the comprehensive, accessible training they need to keep your organization secure.


It’s tough to keep up as criminals reinvent their tactics.
Unfortunately, phishing emails, texts, and bad actors using AI tools represent a significant threat for organizations that are unprepared—particularly those that don’t have a cyber security managed services provider. Human beings are the weakest link in any security program, and that’s especially true when it comes to phishing emails.
Make sure your team is informed, tested, and up-to-date on the latest threats like spear phishing, whaling, smishing, cross-site scripting attacks, and more.


Our team of experts has 250+ combined years of experience keeping businesses safe in this evolving threat landscape. We’ll assess your business for security risks and help you build a proactive plan that keeps you, your employees, and your data secure.
The best part? We offer the only Cybersecurity Service Guarantee in the industry. We cover the cost of our services to remediate an incident, with limitations.
Get the comprehensive cybersecurity team you need for roughly the cost of ONE staff hire. Our team handles monitoring, threat detection, remediation, and more, while you focus on your core business.
Get the security operations center you need with a team that works 24/7/365. Our SOC never sleeps as we protect your data, systems, customers, and internal users from emerging cyber threats.
Are you backing things up as you should? Get peace of mind knowing your data is secure. Our solutions cover two essential components—data backup PLUS disaster recovery plans and processes.
If you can’t detect a cyberattack, you can’t even respond. Managed detection and response gives you the technology, the people, and the monitoring processes to lock down cyberattacks.
Who’s checking your patches? Do they have the time and energy for this essential function? Let our team manage your patching (Windows and third party) so you can focus on your core business.
Are you easy to hack? How would you even know before the unthinkable happens? Penetration testing puts your systems through a rigorous evaluation. You get actionable steps to improve security.
Regulatory compliance is challenging in today’s complex technology environment. Get the managed services you need to achieve continuous IT compliance with your framework or standard.
It’s impossible to eliminate risk. But what if you could quantify it—PLUS define a threshold of acceptable risk and take action to improve? It all starts with a cybersecurity risk assessment from our team.
Cybersecurity awareness training is an educational process that empowers users to detect and respond to common cyber threats. This type of training usually covers topics such as social engineering, pretexting, and phishing–including specific types of phishing such as whaling, spear phishing, smishing, and executive impersonation.
Companies choose to engage in cybersecurity awareness training for a variety of reasons.


Phishing is a social engineering tactic cybercriminals use to lure sensitive data via emails. Take our Quiz & see if you recognize phishing red flags.

Download phishing examples Can your employees spot a phishing email? One of the best ways to avoid getting tricked is to know the red flags

💡 EXCLUSIVE Guide: Phishing Email Examples Download Now Last updated February 27, 2026. If you’ve ever received an “urgent” email that didn’t quite seem legitimate,

The easiest way for cyberattackers to infiltrate an organization is through your employees. And phishing emails continue to get more convincing, especially with the help

Phishing is a social engineering tactic used by hackers to gain access to a network through an unsuspecting email click or attachment download. Since 91% of

Knowing how to spot phishing attacks is the best defense against falling victim to them. Keep your business network safe using these tips.
Watch to learn more about what a SOC is and the role it plays in keeping businesses up and running. A Security Operations Center is the reporting point for a lot of different toolsets. A firewall or antivirus is no longer enough to protect your business. Advanced monitoring toolsets and techniques are required to detect and remediate cybersecurity threats.
Fill out this form, and we’ll respond within one business day. Let’s explore how we can support your business with robust cybersecurity services.
Large enterprises typically have the resources they need to hire cybersecurity experts in-house.
For the rest of us, it’s tough to keep up with cybersecurity. A good MSSP (managed security services provider) is flexible, ready to provide fully managed services (if you don’t have a team) or co-managed services alongside existing staff. It’s all about covering your gaps.
In fact, a comprehensive MSSP steps in exactly where they’re needed. If the company also handles other disciplines, as Corsica does, they can provide diverse services such as:
If you need help with any of the above, a service provider like Corsica is the answer. That’s why we’re here!
Look for a partner who meets your needs in two essential ways:
Both components are critical. A partner can have all the right capabilities and services, but if they’re a real pain to work with, the relationship may cause more headaches than it’s worth.
On the other hand, a partner could be great to work with—but if they have inexperienced technicians or they don’t cover all your needs, then things still aren’t working.
In terms of capabilities and services, look for a partner who covers all your needs:
In terms of finding a provider who acts as a true partner, look for these characteristics:
Here at Corsica Technologies, we’ve got it all covered. From unlimited services to predictable pricing and a “can-do” company culture, we’re making life easier for the people we serve. Contact us today to see what life could look like as a Corsica client.
Most MSSPs claim to be a true partner, but they don’t deliver. Rather than valuing the relationship, they nickel-and-dime their clients when it comes to billing. Fluctuating ticket counts and workstations can create unpredictable invoices. This helps the service provider—but it doesn’t help you.
That’s why we’re fixing the cybersecurity support experience for companies that deserve better. We are the only managed service provider to offer unlimited technology services for one predictable price. That’s what makes us so different. It’s really that simple!
As far as our specific services, we cover essential initiatives like IT, cybersecurity, and digital transformation—but we also cover more technologies than most MSPs do. We also handle EDI and data integration services, which are highly specialized.
In other words, you can hand off as much of your technology to us as you want. And you can do it for one simple monthly price.
So no. We’re not just another MSP.
Want more details? See how Corsica compares to the alternatives.
Yes! We’re one of the few technology service providers who covers EDI solutions in addition to standard services like IT and cybersecurity support. Our career experts in EDI work closely with our cyber and IT teams to ensure all your essential systems run smoothly—with a strong security practice at the core.
In fact, this is one of your biggest advantages. It allows you to work with one provider instead of acting as a referee between different partners who don’t care about mutual success. Here’s how our coverage looks:
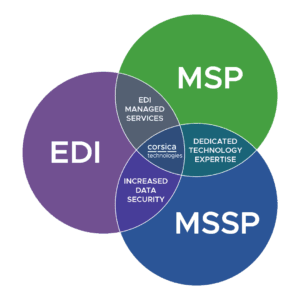
Absolutely! Our services are flexible. We can cover all your needs in a “fully managed” scenario—or we can act as an extension of your staff in a “co-managed” scenario. It all comes down to what resources you have today, what you need, and where your gaps and goals are.
Yes! Our services are designed to work around your needs. We are the team that will say YES to your requirements and what you need. We realize that when you need technology support you need a team that will respond and resolve quickly.
Contact us and let us know what you’re looking for.
Cybersecurity is a distinct need that requires constant monitoring as well as a strong strategy. If a threat arises, there’s no time to assemble a team to get up to speed. You need that team in place, and they need sophisticated tools to detect threats, respond, and defend your business. This is why companies turn to a cybersecurity service provider for help.
Absolutely! Our flagship service package, Corsica Secure, includes consulting from a vCIO/vCISO (virtual CIO/CISO). This C-level leader is a career expert in technology who works alongside you to plan out a 3-year technology roadmap, ensuring you never get blindsided by a technology investment.
We also offer project-driven consulting outside of our recurring services. Just get in touch with us to learn more!
Great question. Everything we do is ultimately about people, and you’ll see that reflected in our day-to-day interactions. You shouldn’t have to deal with techs who don’t care and can’t actually fix the problem. We only hire next-level humans who are career experts in their fields.
Our team is:
Our internal processes and operations are built for one purpose—to make life easier for you. To facilitate this, every client has expert personnel assigned to their journey:
As far as communication, our team is always available 24/7/365 for any technology problem. Because our pricing is simple, you’ll never get billed more when you need more. It’s all included. This empowers your team to go on doing what they do best—rather than fighting technology problems.
We’ll respond within 1 business day, or you can grab time on our calendar.